Crypto Security Multi-Signature Wallets
Why Multi-Signature Wallets Are Essential for Crypto Security. Imagine a digital vault that’s virtually impenetrable, a fortress safeguarding your crypto assets against theft and compromise. That’s the power of multi-signature wallets. They operate on a principle of shared control, demanding multiple approvals before any transaction is executed. This added layer of security makes them a crucial tool for anyone serious about protecting their digital wealth in the volatile world of crypto.
This article delves into the intricacies of multi-signature wallets, explaining their fundamental workings, highlighting their security advantages, and exploring their diverse applications. We’ll examine the different types of multi-signature schemes, like 2-of-3 and 3-of-5, and demonstrate how they significantly outperform traditional single-signature wallets in terms of security.
Introduction to Multi-Signature Wallets
Multi-signature wallets are a powerful tool in the crypto world, offering a significantly enhanced layer of security compared to traditional single-signature wallets. They introduce the concept of shared control, making it virtually impossible for a single entity to gain unauthorized access to funds. This decentralized approach is particularly valuable for users who want to mitigate the risks associated with losing private keys or experiencing account compromises.The fundamental principle behind multi-signature wallets is the need for multiple parties to authorize a transaction.
Multi-signature wallets are crucial for boosting crypto security, adding an extra layer of protection against hacks and theft. Choosing the right platform for staking your crypto, like The Best Crypto Platforms for Secure and Profitable Staking , is just as important. Ultimately, these secure staking options paired with multi-signature wallets provide the best overall defense for your digital assets.
This shared control drastically reduces the attack surface, making it significantly more difficult for malicious actors to steal funds. Imagine a scenario where access to a cryptocurrency account requires approval from two out of three individuals. This inherently creates a safeguard, making it a more secure alternative to the traditional approach.
Multi-Signature Wallet Functionality
Multi-signature wallets function by requiring multiple digital signatures to authorize a transaction. This cryptographic mechanism ensures that no single party can unilaterally execute a transaction. This is a crucial element of the enhanced security, as compared to single-signature wallets, which rely on only one private key.
Types of Multi-Signature Schemes
Multi-signature schemes are defined by the required number of signatures needed to authorize a transaction. Different schemes cater to various security and control needs.
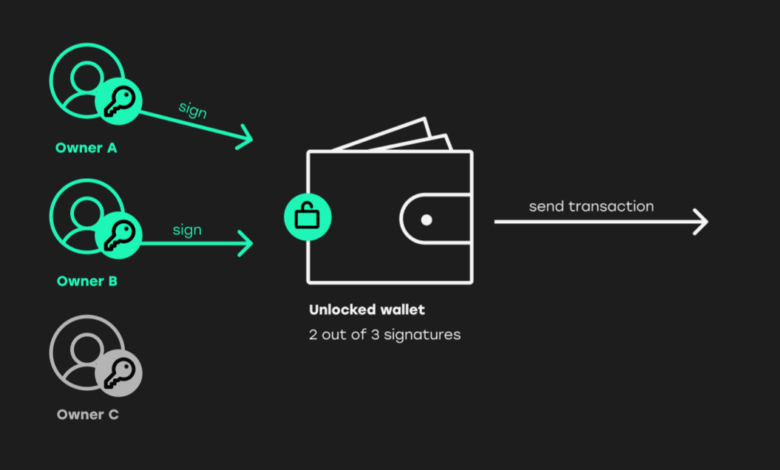
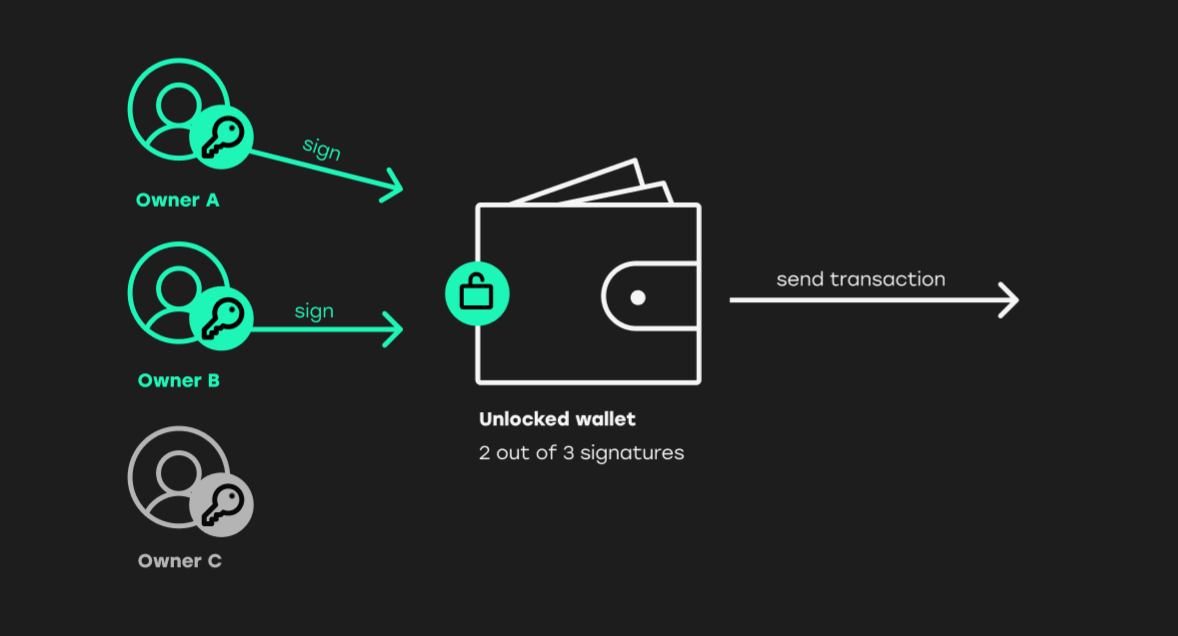
- 2-of-3: This scheme requires two out of three authorized signatories to approve a transaction. This approach provides a good balance between security and ease of access, particularly for collaborative scenarios.
- 3-of-5: This scheme requires three out of five authorized signatories to approve a transaction. The higher threshold provides increased security, but also increases the complexity and coordination required for transaction authorization. This is often suitable for high-value transactions or for situations where a higher degree of security is paramount.
- n-of-m: This is a more general representation of multi-signature schemes. It represents a flexible model where ‘n’ signatures out of ‘m’ participants are required for a transaction. This provides a customizable approach to security based on specific use cases and risk assessments.
Enhanced Security Compared to Single-Signature Wallets
Multi-signature wallets drastically improve security by distributing the control over funds. Traditional single-signature wallets are vulnerable to scenarios where a private key is compromised. This vulnerability opens the door for malicious actors to access and steal funds. Multi-signature wallets effectively mitigate this risk by requiring multiple parties to collaborate for transaction authorization. This layered approach to security is a critical aspect of enhancing the overall safety and reliability of cryptocurrency transactions.For example, a company managing a large cryptocurrency treasury can implement a multi-signature scheme to safeguard funds.
If one employee’s credentials are compromised, the funds remain protected because the necessary signatures from other employees are required. This level of security is a critical component for maintaining trust and confidence in cryptocurrency transactions.
Protecting your crypto is crucial, and multi-signature wallets are a game-changer for security. They essentially require multiple approvals before any transaction can happen, adding an extra layer of protection. This is similar to the benefits of a healthy diet, like incorporating moringa leaves into your daily routine for improved overall well-being, Top Reasons to Include Moringa Leaves in Your Diet for Better Health highlights the power of proactive measures.
Ultimately, multi-signature wallets are an essential tool to safeguard your digital assets from theft and unauthorized access.
Security Advantages of Multi-Signature
Multi-signature wallets offer a significant leap forward in crypto security, moving beyond the vulnerabilities inherent in single-signature systems. By demanding multiple approvals for transactions, they dramatically reduce the risk of unauthorized access and theft. This enhanced security is particularly crucial in the volatile cryptocurrency landscape where malicious actors are constantly seeking opportunities to exploit weaknesses.Requiring multiple signatures creates a robust barrier against theft.
Multi-signature wallets are crucial for crypto security, adding an extra layer of protection against hacks and theft. Knowing how to spot promising low-cap crypto projects before they explode is also key, and a great resource for this is The Secret to Finding Low-Cap Crypto Gems Before They Explode. Ultimately, both strategies help you navigate the volatile crypto market more confidently, ensuring your digital assets are safe and your investments are well-informed.
A single compromised private key no longer grants full access to the wallet’s funds. This layered approach makes it far more difficult for attackers to gain control of the entire balance. The added layer of security translates to peace of mind for crypto users, enabling them to confidently manage their assets without the constant fear of a single point of failure.
Mitigation of Single Point of Failure Risks
Multi-signature wallets effectively eliminate the single point of failure inherent in single-signature wallets. A single compromised private key can lead to the total loss of funds in a single-signature system. With multi-signature, the funds are secured by requiring the combined authorization of multiple parties, drastically reducing the risk of unauthorized access. This decentralized control significantly minimizes the impact of a compromised private key.
Think of it like a team project where multiple people need to sign off on a document before it’s finalized; no single person can act alone.
Impact of Compromised Private Keys
The risk of a compromised private key is drastically reduced with multi-signature wallets. Even if one or more private keys are compromised, the funds remain protected as long as the remaining necessary signatures aren’t also compromised. This crucial feature significantly minimizes the potential financial damage from a security breach. For instance, if a user’s personal computer is hacked and their private key is stolen, the funds in their multi-signature wallet are not immediately at risk unless the attackers can also gain access to the private keys of the other required signatories.
Role of Cryptography in Multi-Signature Transactions
Cryptography plays a critical role in ensuring the validity and security of multi-signature transactions. Cryptographic techniques, such as digital signatures, are used to verify the identity of the signatories and to ensure that the transaction hasn’t been tampered with. These cryptographic methods provide a layer of trust and immutability, making the transaction verifiable and trustworthy. The specific cryptographic algorithms used, like ECDSA, are designed to withstand sophisticated attacks, ensuring that the transaction can only be completed with the appropriate approvals.
“Digital signatures provide authentication and integrity for multi-signature transactions.”
Security Feature Comparison
| Feature | Single-Signature | Multi-Signature |
|---|---|---|
| Required Signatures | 1 | 2 or more |
| Security | Lower | Higher |
| Risk of Compromise | High | Low |
| Key Management | Complex | Easier |
A clear comparison reveals the substantial advantages of multi-signature wallets in terms of security. The table highlights the crucial difference in security and risk mitigation that multi-signature offers. Users can significantly enhance their crypto security by adopting these more secure practices.
Practical Applications and Use Cases: Why Multi-Signature Wallets Are Essential For Crypto Security
Multi-signature wallets are no longer a niche technology. Their robust security features make them increasingly valuable for a wide range of applications, from personal asset protection to complex business transactions. Understanding the diverse use cases illuminates the practical benefits of this cryptographic approach.Multi-signature wallets offer a layered approach to security, dramatically reducing the risk of unauthorized access compared to traditional single-signature wallets.
This inherent security translates into practical applications across various sectors, making them a powerful tool for individuals and businesses alike.
Joint Account Management
Shared access to funds is a common need for families, business partners, and even estate planning. Multi-signature wallets provide a secure way to manage these joint accounts. Each signatory requires approval before any transaction can be executed, ensuring that no single individual can unilaterally control the funds. This is especially beneficial for situations where multiple parties need to agree on transactions, preventing accidental or malicious misuse of the funds.
For example, a family might set up a multi-signature account for managing a child’s college fund, requiring both parents’ approval for withdrawals.
Business Transactions
Businesses handling sensitive transactions, such as cryptocurrency exchanges or high-value investments, benefit greatly from multi-signature wallets. The enhanced security provided by requiring multiple signatures makes it considerably more difficult for hackers or rogue employees to compromise the funds. Furthermore, the transparency and auditability inherent in multi-signature transactions can help mitigate financial risks and enhance trust amongst stakeholders. For instance, a venture capital firm managing substantial investments in crypto startups might use multi-signature wallets to ensure that every significant transaction is authorized by multiple board members.
Custodial Services
Custodial services, which manage cryptocurrency assets for clients, rely heavily on multi-signature wallets for enhanced security. By implementing multi-signature protocols, custodians reduce the risk of account compromise significantly. The added layer of security provided by requiring multiple approvals mitigates the risk of fraudulent activity and ensures the safety of client funds. This is particularly critical in the realm of cryptocurrency, where the potential for theft and fraud is significant.
Asset Protection
Multi-signature wallets are crucial for safeguarding valuable assets. The complexity of these protocols adds a considerable deterrent to theft, making them an ideal solution for individuals with substantial cryptocurrency holdings. The additional layer of security provided by multi-signature wallets protects against unauthorized access, and significantly increases the overall security of assets. For example, individuals with large portfolios of rare NFTs might utilize multi-signature wallets to ensure the security of their digital assets.
Cold Storage, Why Multi-Signature Wallets Are Essential for Crypto Security
Multi-signature wallets are highly beneficial for cold storage strategies. By storing the private keys offline, the risk of compromise through hacking or malware is minimized. The addition of multiple signatures further enhances security. The combination of offline storage and multi-signature protocols significantly reduces the risk of unauthorized access, protecting assets from theft.
Specific Use Cases for Multi-Signature Wallets
| Use Case | Advantages |
|---|---|
| Joint Account Management | Secure shared access to funds, requiring agreement from multiple parties before transactions |
| Business Transactions | Enhanced security for sensitive transactions, preventing unauthorized access and fraudulent activity |
| Custodial Services | Reduced risk of account compromise, ensuring client funds are protected from theft or fraud |
| Asset Protection | Safeguarding valuable assets, providing multiple layers of security against unauthorized access |
Implementation Considerations
Setting up a multi-signature wallet requires careful planning and execution. The process involves generating and managing multiple private keys, ensuring secure storage, and backing up the wallet’s data. Choosing the right platform is crucial for ease of use and security. Understanding these steps is essential for safeguarding your cryptocurrency assets.The security of your multi-signature wallet hinges on the meticulous implementation of these procedures.
Properly managing private keys, securing storage, and establishing robust backup protocols are paramount to maintaining the integrity and accessibility of your funds. Each step contributes to the overall resilience of your digital asset holdings.
Setting Up a Multi-Signature Wallet
The setup process varies depending on the chosen platform, but generally involves these key steps:
- Selecting a Platform: Choose a reputable multi-signature wallet platform that aligns with your needs and security requirements. Research platform security audits and user reviews.
- Generating Private Keys: Generate multiple private keys, each controlled by a different party. The number of keys and parties involved determines the level of security and access required. For example, a 2-of-3 multi-signature wallet requires two out of three parties to approve transactions.
- Adding Parties: Invite the parties involved to the wallet. The platform usually provides an interface for adding each party’s public key. Clear communication is vital for successful wallet setup.
- Defining Transaction Rules: Specify the rules for transaction authorization. For example, in a 2-of-3 scenario, any two of the three parties must approve a transaction.
Generating and Managing Multiple Private Keys
Managing multiple private keys requires a systematic approach to prevent errors and maintain security.
- Key Management Software: Utilize dedicated software for managing private keys securely, such as hardware wallets or specialized key management tools. This safeguards against accidental loss or compromise of individual keys.
- Storing Keys Securely: Avoid storing private keys on easily accessible devices or online platforms. Employ strong password protection and consider hardware wallets for enhanced security.
- Mnemonic Phrases: For offline key generation, use mnemonic phrases, which are memorable sequences of words representing private keys. Write these down and store them in a secure, offline location.
Secure Key Storage and Management Practices
Robust key management practices are critical for maintaining the security of your multi-signature wallet.
- Hardware Wallets: Utilize hardware wallets, which are physical devices designed for secure key storage. These devices provide an extra layer of security against online threats.
- Offline Storage: Store private keys and backup data offline to protect against unauthorized access to your system.
- Password Managers: Employ strong passwords and use reputable password managers to keep track of access credentials.
Securing and Backing Up Wallet Data
Regular backups and security measures are crucial for the long-term integrity of your multi-signature wallet.
- Regular Backups: Regularly back up the wallet’s data, including private keys, on a separate, secure device. This ensures data recovery in case of device loss or system failure.
- Secure Backup Storage: Store backups in a secure, offline location, such as a physical hard drive or a cloud storage service with strong encryption. Use a reputable cloud provider and implement multi-factor authentication.
- Version Control: Maintain versions of your wallet’s data to enable easy restoration to previous states.
Comparing Multi-Signature Wallet Platforms
Different platforms offer varying features and security levels.
| Platform | Features | Security |
|---|---|---|
| Platform A | Intuitive interface, strong security protocols | High |
| Platform B | Advanced features, robust key management tools | High |
| Platform C | Focus on ease of use | Moderate |
Note: This is a simplified comparison. Thorough research is necessary to evaluate specific platforms.
Creating a 2-of-3 Multi-Signature Wallet
This Artikels the steps to create a 2-of-3 multi-signature wallet:
- Select a platform: Choose a reliable multi-signature wallet platform that supports 2-of-3 setups.
- Generate Private Keys: Create three private keys.
- Add Parties: Invite the three parties to the wallet, providing each with their respective public key.
- Define Transaction Rules: Set the rule requiring two out of three signatures for transaction approval.
- Secure Storage: Securely store each party’s private key, and backup the wallet data as instructed by the platform.
Challenges and Limitations of Multi-Signature Wallets

Source: oneart.digital
Multi-signature wallets, while enhancing security, introduce a new set of complexities. Their inherent design, relying on multiple parties for authorization, can present practical hurdles for both users and developers. Understanding these limitations is crucial for effective implementation and mitigating potential risks.
Key Management Complexity
Managing multiple private keys for a multi-signature wallet is significantly more complex than managing a single key. Each keyholder needs secure storage and access to their private keys, which requires robust security measures. This increased complexity necessitates sophisticated key management systems and protocols to prevent unauthorized access and maintain operational efficiency. Furthermore, ensuring that all parties involved have access to the necessary keys and can communicate effectively is paramount.
Compromising a single key can render the entire wallet vulnerable, highlighting the importance of secure storage and access control for each private key.
Transaction Speed and Communication Protocols
Multi-signature transactions are inherently slower than single-signature transactions. The need for multiple approvals introduces a delay. This delay can be significant, especially in environments with high transaction volumes or strict latency requirements. The time required for each party to verify and authorize a transaction can accumulate, potentially impacting the overall transaction speed. Consequently, optimized communication protocols and efficient signature verification mechanisms are crucial for minimizing transaction processing times.
Communication Risks
Secure communication channels are essential for verifying signatures in multi-signature wallets. Compromised communication channels, whether through malicious attacks or technical failures, can lead to security breaches. For instance, a compromised network could allow attackers to intercept and manipulate communication between parties, potentially leading to unauthorized transactions. To mitigate this risk, it’s imperative to utilize secure communication protocols like TLS (Transport Layer Security) to encrypt communication channels.
Potential Delays in Transaction Processing
The multi-signature verification process can introduce significant delays. Each participant needs to verify the transaction, potentially requiring the involvement of multiple parties located in different geographical regions. This can increase the time required to complete a transaction, particularly in scenarios involving several keyholders or complex approval processes. Consequently, users should consider the potential transaction delays when choosing a multi-signature wallet and should select wallets with optimized communication protocols and secure infrastructure to reduce transaction times.
Summary of Challenges and Limitations
| Challenge | Description | Mitigation Strategy |
|---|---|---|
| Key Management | Managing multiple keys can be complex, requiring robust security measures for each keyholder. | Employ secure key management tools, such as hardware security modules (HSMs) or dedicated key management systems. |
| Transaction Speed | Transactions can be slower due to the need for multiple approvals and verification steps. | Optimize communication protocols and use efficient signature verification algorithms. |
| Communication Risks | Compromised communication channels can lead to security breaches and unauthorized transactions. | Employ secure communication channels (e.g., encrypted connections) and robust authentication protocols. |
Illustrative Examples of Multi-Signature Wallets
Source: webflow.com
Multi-signature wallets, with their inherent security features, are finding increasing applications in various sectors. Beyond individual use, they’re proving crucial for safeguarding assets in corporate environments and bolstering security in decentralized finance (DeFi). These wallets offer a robust defense against unauthorized access, making them an essential tool in today’s digital landscape.
Real-World Applications of Multi-Signature Wallets
Multi-signature wallets are gaining traction across diverse sectors. They’re not just for individual crypto enthusiasts but also vital for corporate treasuries and DeFi platforms. Their ability to distribute control significantly enhances security, preventing single points of failure.
- Corporate Treasuries: Many large corporations, especially those dealing with substantial crypto holdings, utilize multi-signature wallets to protect their assets. A typical scenario involves a multi-signature system for crucial transactions like transferring large amounts of cryptocurrency, which requires authorization from multiple authorized signatories. This reduces the risk of unauthorized withdrawals and ensures accountability, safeguarding the company’s funds.
- Decentralized Finance (DeFi): DeFi protocols often rely on multi-signature wallets to secure their funds and facilitate secure transactions. Smart contracts are frequently involved, and these wallets are crucial for safeguarding the assets and mitigating risks associated with DeFi operations. This approach is essential for the integrity and security of the entire ecosystem.
Case Studies of Successful Implementations
While specific case studies are often proprietary, many examples exist within the corporate sector. A successful implementation involves careful planning and consideration of the specific security needs and compliance requirements.
- Example: A large financial institution might use a multi-signature wallet to manage cryptocurrency reserves. This wallet could be configured with multiple signatories, each representing a different department or security level. This layered authorization drastically reduces the risk of unauthorized transactions.
Multi-Signature Wallets in Corporate Treasuries
In the corporate world, multi-signature wallets are invaluable for managing substantial cryptocurrency holdings. Their ability to distribute control among multiple parties minimizes the risk of unauthorized access, aligning with strict compliance standards.
- Security Enhancement: The distributed nature of multi-signature wallets ensures that no single individual or entity has complete control. This is a critical aspect for compliance, preventing fraud and reducing the chances of financial irregularities.
- Enhanced Compliance: Corporations operating in regulated environments often require multi-signature wallets for compliance reasons. These wallets adhere to regulatory requirements by documenting all transactions and approvals.
Contribution to Enhanced Security in Decentralized Finance
Multi-signature wallets play a critical role in enhancing the security of decentralized finance (DeFi) protocols. The distributed nature of these wallets minimizes the risk of a single point of failure and prevents unauthorized access to funds.
- Risk Mitigation: Multi-signature wallets reduce the risks associated with single points of failure. This is especially crucial in the DeFi space, where smart contracts and automated transactions are prevalent.
- Transaction Integrity: Multi-signature wallets guarantee that all transactions adhere to the defined protocol and rules. This ensures the integrity of the DeFi ecosystem.
Multi-Signature Transaction Flow Illustration
A multi-signature transaction typically involves these steps:
- Initiation: A transaction request is initiated by one party.
- Verification: The request is sent to all designated signatories for verification.
- Approval: Each signatory approves the transaction based on predefined criteria.
- Transaction Execution: If all signatories approve, the transaction is executed.
- Record Keeping: All approvals and transaction details are meticulously recorded for auditing and compliance purposes.
Security Implications of Cryptographic Algorithms
The choice of cryptographic algorithms directly impacts the security of multi-signature wallets. Different algorithms offer varying levels of security and resilience against attacks.
- Elliptic Curve Cryptography (ECC): ECC is a widely used algorithm in multi-signature wallets due to its efficiency and security properties. It’s considered a strong choice for generating keys and ensuring the integrity of transactions.
- Hashing Algorithms: Secure hashing algorithms like SHA-256 are crucial for verifying the integrity of transaction data. A compromised hashing algorithm can lead to data manipulation and compromise the security of the entire system.
Ultimate Conclusion
In conclusion, multi-signature wallets are a critical component of a robust crypto security strategy. Their ability to distribute control and mitigate risks makes them an essential tool for both individual investors and businesses dealing with digital assets. While there are challenges like key management complexity, the advantages of heightened security and reduced vulnerability far outweigh the drawbacks. By understanding the nuances of these wallets, you can significantly enhance your crypto security posture and protect your valuable digital holdings.
Quick FAQs
What are some common use cases for multi-signature wallets beyond personal use?
Businesses frequently use multi-signature wallets for joint account management, ensuring that multiple authorized parties must agree on transactions. This is crucial for minimizing fraud risks and safeguarding company funds. They’re also beneficial in custodial services, where reduced risk of account compromise is paramount. In short, any scenario involving shared access or high-value assets benefits from the enhanced security.
How do I choose the right multi-signature wallet platform?
Consider factors like security protocols, ease of use, transaction fees, and the number of supported cryptocurrencies. Read reviews and compare features before making a decision. User experience and customer support are also important aspects to evaluate.
What are the potential drawbacks of using multi-signature wallets?
Transaction speed can be slower due to the need for multiple approvals. Managing multiple private keys can be more complex than managing a single key. Furthermore, a compromised communication channel can put the entire system at risk. However, these potential downsides are often outweighed by the significant improvement in security.
What’s the difference between a 2-of-3 and a 3-of-5 multi-signature wallet?
The numbers in these schemes (e.g., 2-of-3, 3-of-5) represent the required number of signatures needed to authorize a transaction. A 2-of-3 scheme requires two out of three parties to approve, while a 3-of-5 scheme requires three out of five parties to agree. The higher the number, the more secure the wallet, but potentially slower the transaction process.