Spotting Fake Crypto How to Detect and Avoid
How to Detect and Avoid Fake Crypto Exchanges and Projects is crucial in today’s crypto landscape. Navigating the world of digital currencies requires vigilance, as fraudulent exchanges and projects are unfortunately prevalent. This guide will equip you with the knowledge and tools to identify red flags, assess project legitimacy, evaluate security measures, research communities, and leverage external resources, ultimately empowering you to make informed decisions and protect your investments.
From identifying suspicious exchange listings to evaluating project white papers and security measures, this comprehensive guide provides actionable steps to avoid falling victim to scams and fraudulent activities. We’ll delve into specific red flags, provide practical checklists, and offer real-world examples to illustrate the techniques. This detailed analysis will allow you to differentiate between legitimate and fraudulent ventures, helping you navigate the complexities of the crypto market with confidence.
Identifying Red Flags in Exchange Listings: How To Detect And Avoid Fake Crypto Exchanges And Projects
Navigating the cryptocurrency landscape can be daunting, especially when dealing with numerous exchanges and projects. Many fraudulent exchanges and projects are designed to mimic legitimate platforms, making it crucial for investors to be vigilant and identify potential red flags. This section will delve into common indicators of fraudulent exchanges and the importance of verifying their legitimacy.Scammers often employ sophisticated techniques to lure investors into their traps.
Recognizing these tactics is vital to protect your investments and avoid becoming a victim. Knowing the red flags and understanding the mechanisms behind these scams will empower you to make informed decisions.
Common Red Flags in Exchange Listings
Recognizing red flags in exchange listings is crucial for protecting your investment. A thorough examination of the platform and its associated information is essential before engaging. Below are ten common red flags to watch out for:
- Suspicious or vague information about the exchange’s history and ownership.
- Lack of transparency regarding the exchange’s security measures and operational structure.
- Rapid or unusual price fluctuations of listed cryptocurrencies.
- Claims of exceptionally high returns or guaranteed profits.
- Pressure to invest quickly without proper due diligence.
- Limited or no customer support channels.
- Use of complex or jargon-filled language to obscure the exchange’s true nature.
- Unusually high transaction fees or hidden charges.
- Difficulty in withdrawing funds.
- Sudden and unexplained removal of cryptocurrencies from the exchange.
These red flags often accompany deceptive practices used by scammers, such as creating fake websites that mirror legitimate exchanges, using misleading advertisements, and manipulating market prices. These practices are designed to exploit investors’ lack of knowledge or eagerness to profit.
Verifying Exchange Licenses and Regulatory Compliance
Legitimate cryptocurrency exchanges often comply with local and international regulations. Verifying an exchange’s license and regulatory compliance is paramount for your safety. This verification helps ensure that the exchange operates within established standards and protects user funds. Finding this information involves a meticulous approach:
- Consult official regulatory bodies: Look for regulatory bodies in the jurisdiction where the exchange claims to be registered or licensed. Their websites often list registered exchanges.
- Examine the exchange’s official website: A reputable exchange will prominently display its license and regulatory information on its website. Scrutinize the information for authenticity and validity.
- Cross-reference information: Double-check the information from the exchange’s website against the official regulatory bodies’ databases to confirm its accuracy.
Comparing Legitimate and Fraudulent Exchanges
The following table Artikels key distinctions between legitimate and fraudulent exchanges:
| Feature | Legitimate Exchange | Fraudulent Exchange |
|---|---|---|
| Security | Robust security measures, such as multi-factor authentication (MFA) and encryption protocols, are implemented. Audits are often available. | Minimal or no security measures. Data breaches and fund loss are common. |
| User Interface | User-friendly and intuitive interface. Clear and concise information is provided. | Clunky or poorly designed interface with confusing information. |
| Support | Prompt and responsive customer support channels, such as email, live chat, or phone. | Limited or non-existent customer support. Responses are delayed or unhelpful. |
| Payment Options | Wide range of secure payment methods. Details are clearly displayed. | Limited or obscure payment options. Details are unclear. |
Common Fraudulent Practices on Cryptocurrency Exchanges
Fraudulent exchanges often utilize various deceptive practices. Awareness of these tactics is essential for investors to protect themselves.
| Practice | Description | Example |
|---|---|---|
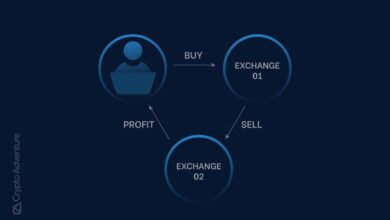
| Pump and Dump Schemes | Deliberate manipulation of cryptocurrency prices to attract investors, followed by a rapid price drop. | A fake exchange artificially inflates the price of a newly listed cryptocurrency, then sells it at the inflated price, causing the price to crash. |
| Fake Listings | Listing non-existent or fraudulent cryptocurrencies to attract investors. | Listing a token that does not exist or has no real backing. |
| Phishing Attacks | Attempting to trick users into revealing sensitive information, such as passwords and private keys. | Sending fraudulent emails or messages that appear to be from the exchange, requesting login credentials. |
Assessing Project Legitimacy
Unveiling the truth behind a cryptocurrency project requires more than just a catchy name and impressive visuals. Thorough investigation into the project’s foundations is paramount to avoid falling victim to scams. This section delves into crucial criteria for evaluating a project’s legitimacy, highlighting common red flags and providing a practical checklist for informed decision-making.Evaluating a project’s legitimacy goes beyond surface-level analysis.
It demands a deep dive into the project’s fundamentals, examining its team, white paper, roadmap, and tokenomics. This meticulous process helps distinguish between legitimate ventures and fraudulent schemes, ultimately safeguarding your investment.
Key Criteria for Project Legitimacy
Understanding the fundamental aspects of a project is critical to its assessment. These factors are the building blocks of evaluating any project, helping you distinguish genuine endeavors from fraudulent attempts. The following five criteria offer a robust framework:
- Team Expertise and Background: A reputable project boasts a team with demonstrable expertise in the relevant field. Investigate the team’s prior experience, academic qualifications, and contributions to the blockchain or cryptocurrency industry. Look for a diverse skill set encompassing technical development, marketing, and business acumen. Beware of teams with minimal or fabricated backgrounds, as this often indicates a high-risk project.
- Comprehensive Market Analysis: A legitimate project thoroughly analyzes the target market, identifies the problem it intends to solve, and presents a viable solution. A strong market analysis demonstrates a clear understanding of user needs and competitive landscape. Look for a well-researched, data-driven approach, rather than unsubstantiated claims or vague promises.
- Detailed Technical Documentation: Scrutinize the project’s technical documentation, including white papers and smart contract code. A clear and well-structured white paper should Artikel the project’s vision, technical architecture, and tokenomics. The smart contract code should be auditable and demonstrate the security of the project. Avoid projects with poorly documented or inaccessible technical information.
- Realistic Roadmap and Tokenomics: A realistic roadmap provides a clear, attainable progression of milestones. A meticulously Artikeld roadmap, including timelines and key metrics, is crucial. Examine the project’s tokenomics, ensuring the token distribution, utility, and value proposition align with market trends and are not excessively inflated or overly complex. Avoid projects with unrealistic timelines or vague plans.
- Active and Engaged Community: A robust and active community provides a vital gauge of a project’s credibility. Analyze the level of engagement and interaction among members. A vibrant community fosters collaboration and builds trust, unlike a project with minimal or suspicious engagement. Be wary of overly enthusiastic or artificially inflated communities.
Identifying Project Scams Through White Papers
Project white papers serve as the foundational documents outlining a cryptocurrency project’s goals and strategies. Critically evaluating these documents is essential for identifying potential scams.
- Red Flags in White Papers: Look for vague or contradictory statements, unrealistic promises, lack of technical details, and missing or poorly explained tokenomics. Beware of overly optimistic projections, insufficient market analysis, and a lack of transparency regarding team members.
- Analyzing Roadmap and Tokenomics: A project’s roadmap should be detailed and realistic, outlining milestones and timelines. A well-structured roadmap avoids overly ambitious timelines or unrealistic promises. Scrutinize the tokenomics, ensuring the token’s utility and value proposition are aligned with the project’s goals and are not overly complex or inflated. Examine the token distribution plan, focusing on fair distribution and transparency.
Project Legitimacy Evaluation Checklist
This checklist provides a structured approach to evaluating a cryptocurrency project’s legitimacy.
| Criteria | Evaluation Points |
|---|---|
| Team Background | Experience, qualifications, contributions to the blockchain space, team members’ backgrounds, and past projects. |
| Market Analysis | Thoroughness of market research, identification of target audience, and a clear problem-solution approach. |
| Technical Documentation | Clarity of white paper, smart contract code auditability, and technical feasibility. |
| Community Engagement | Level of engagement, active participation, and transparency of the community. |
Comparing Legitimate and Fraudulent Project Websites
A project’s website often provides the first impression. Legitimate and fraudulent websites exhibit stark differences in design, transparency, and user interaction.
- Legitimate Websites: These websites generally feature a clean and professional design, providing clear and concise information. Transparency is paramount, including details about the team, technology, and roadmap. User interaction is often facilitated by interactive elements, such as contact forms and FAQs.
- Fraudulent Websites: These websites often display a flashy, unprofessional design with vague information and exaggerated claims. Transparency is lacking, with limited information regarding the team, technology, and roadmap. User interaction is limited, with minimal or no contact channels.
Evaluating Security Measures
Protecting your cryptocurrency investments requires a multi-layered approach, focusing not only on identifying fraudulent exchanges and projects but also on implementing robust security measures for your own digital assets. Understanding the different types of wallets and their security characteristics, along with implementing strong security practices, is crucial in safeguarding your holdings from theft and fraud. This section delves into the importance of secure wallets, exchange security protocols, and personal security measures to ensure your crypto journey is safe and profitable.Robust security practices are paramount when dealing with cryptocurrency.
The digital nature of these assets necessitates a high degree of vigilance and proactive measures to protect them from malicious actors. The focus now shifts to understanding and implementing the necessary security protocols to protect your crypto assets.
Secure Wallets and Their Importance
Cryptocurrency wallets are the digital containers for your holdings. They act as your personal accounts, holding your private keys that grant access to your funds. Choosing the right wallet type is crucial to maintaining your financial security.
- Hardware Wallets: These physical devices are considered the most secure option. They store your private keys offline, effectively isolating them from online threats. They are generally more resistant to hacking and malware. However, they may be more expensive and require a learning curve for initial setup.
- Software Wallets: These wallets reside on your computer or mobile device. They provide convenience and ease of use, often with user-friendly interfaces. Their security depends heavily on the platform’s security measures and the user’s vigilance in protecting their devices and passwords. Compromised devices can expose your funds to theft.
- Web Wallets: These wallets reside on a website or platform. They offer ease of use, often integrating with other financial services. However, they present the highest risk as your funds are stored on a remote server, making them vulnerable to hacking and platform outages.
Identifying Robust Security Measures on Exchanges
Exchange security plays a critical role in protecting your assets. Look for exchanges that implement strong security protocols.
- Encryption Protocols: Robust encryption protocols, such as TLS 1.2 or higher, are essential for safeguarding data in transit. They ensure that communications between your device and the exchange are unreadable to unauthorized parties. Look for exchanges explicitly mentioning the encryption protocol they use. Older protocols are more vulnerable.
- Multi-Factor Authentication (MFA): Implement MFA whenever possible. This adds an extra layer of security, requiring a secondary verification method beyond a password, such as a code from a dedicated app or a text message. This significantly reduces the risk of unauthorized access.
Securing Your Cryptocurrency Holdings
Safeguarding your cryptocurrency involves proactive steps that go beyond simply choosing a secure wallet.
- Backup Your Wallets: Regularly back up your wallets, particularly hardware wallets. This creates a secondary copy of your private keys in case of loss or damage to your primary device.
- Strong Passwords: Use strong, unique passwords for all your accounts. Consider using a password manager to help generate and store these passwords securely.
- Avoid Phishing Attempts: Be highly vigilant against phishing attempts. Phishing attacks often mimic legitimate exchange platforms or services. Be wary of unsolicited emails, messages, or links. Verify the authenticity of communications and never share your private keys or login information through suspicious channels.
Spotting Potential Phishing Attempts
Phishing scams are common in the cryptocurrency space, targeting investors with misleading communications.
- Fake Exchange Sites: Be wary of websites that closely resemble legitimate cryptocurrency exchanges. Check for misspellings, unusual formatting, or security certificates. Do thorough research before entering any personal information.
- Malicious Links: Be extremely cautious of any links that seem suspicious or unfamiliar. Hover over links before clicking to see the actual destination URL. A slight difference in the URL can indicate a phishing attempt.
- Impersonation: Scammers often impersonate trusted individuals or organizations. Do not trust communications without verifying the sender’s identity independently. Look for official announcements or communication channels from verified sources.
Researching Community and Social Proof
Cryptocurrency projects often rely heavily on community engagement and social proof to build trust and attract investors. A vibrant and active community can signal project legitimacy and support, while a lack of engagement can raise red flags. However, it’s crucial to differentiate between genuine enthusiasm and fabricated activity. Understanding how to assess these indicators is essential for discerning legitimate projects from scams.Assessing community engagement is vital for evaluating a cryptocurrency project’s viability.
Spotting fake crypto exchanges and projects is crucial, especially as more countries explore adopting cryptocurrency as legal tender, like those discussed in this insightful article: Why More Countries Are Adopting Cryptocurrency as Legal Tender. Look for red flags like unrealistic promises and lack of transparency. Thorough research and due diligence are key to avoiding scams, even when the allure of quick gains is strong.
A project with a large, active, and engaged community is more likely to succeed, as this signifies broad interest and support. Conversely, a project with minimal or no community interaction can suggest a lack of genuine interest or even a coordinated effort to artificially inflate the project’s value.
Assessing Community Engagement
Genuine communities demonstrate consistent interaction, thoughtful discussions, and a shared vision. Look for organic conversations, not just promotional posts or repetitive messages. Projects with genuine communities often have members who contribute actively to discussions, provide constructive feedback, and engage with the project’s development. Observe if the community members are diverse in their backgrounds and experiences. A diverse community suggests wider appeal and support.
Identifying Fake Communities
Fake communities often exhibit unusual characteristics, including a disproportionate ratio of promotional content to genuine discussions. A high volume of automated messages, bots, or identical accounts can indicate a coordinated effort to artificially inflate engagement. Examine the content quality and the overall tone of the community discussions. If the conversations are superficial or lack substance, it could be a sign of manipulation.
Spotting fake crypto exchanges and projects is crucial, especially as Web3 technology transforms how we use digital money. Understanding the risks is key, and learning how to verify platforms is essential. This is where thorough research comes in handy, and checking reviews from reputable sources is a great starting point. For a deeper dive into how Web3 is changing the digital money landscape, check out this insightful article: Why Web3 Technology is Changing How We Use Digital Money.
Ultimately, staying vigilant and questioning everything is the best defense against these fraudulent ventures.
Comparing Legitimate and Fraudulent Communities
| Feature | Legitimate Project | Fraudulent Project |
|---|---|---|
| Engagement | High level of organic interaction, diverse discussions, and active participation from multiple users. | High volume of automated messages, repetitive posts, or a significant number of inactive accounts. Engagement is often concentrated in a small group of users. |
| Content Quality | High-quality, well-researched content, insightful discussions, and constructive feedback. Content addresses project updates and community concerns. | Low-quality, generic content, superficial discussions, and a lack of substance. Content often focuses on promoting the project rather than providing information. |
| Overall Tone | Positive, constructive, and supportive tone. Members express enthusiasm for the project while also addressing concerns. | Aggressive, overly enthusiastic, or even aggressive tone. Members may engage in aggressive promotion or attack those who raise doubts. |
Indicators of Manipulation
Several indicators can suggest a coordinated attempt to artificially inflate project value or engagement:
- Sudden, dramatic increases in social media followers or engagement. This is particularly suspicious if the increase is not accompanied by a corresponding increase in genuine user activity.
- High concentration of accounts with similar or identical profiles and activity patterns. This can indicate coordinated efforts to create a false sense of community.
- Coordinated and synchronized messaging. Look for patterns in the timing and content of posts and comments. Coordinated posting often indicates a coordinated attempt to promote the project or mislead investors.
- A disproportionate ratio of promotional content to genuine discussions. A project that focuses heavily on promoting its own merits, rather than engaging in discussion or providing information, is a significant red flag.
By carefully examining the community surrounding a cryptocurrency project and identifying potential red flags, investors can significantly reduce their risk of falling victim to scams and fraudulent projects.
Using External Resources for Verification

Source: web-mind.io
Verifying the legitimacy of crypto exchanges and projects requires a multi-faceted approach. Simply relying on claims made by the project or exchange is insufficient. Thorough investigation using external resources is crucial to identify potential red flags and ensure the safety of your investments. This involves examining transactions, project information, and the overall reputation surrounding the project or exchange.External resources provide a crucial layer of verification beyond the information presented by the exchange or project.
These resources allow you to cross-reference claims and uncover potential inconsistencies or misleading information. Using reputable blockchain explorers, news sources, and regulatory databases helps build a comprehensive picture of the project’s activities and the exchange’s trustworthiness.
Using Blockchain Explorers
Blockchain explorers are invaluable tools for verifying transaction history and project activity. These platforms provide detailed information about cryptocurrency transactions, allowing you to trace the movement of funds and identify potential anomalies.
Step-by-Step Guide:
- Select a reputable blockchain explorer. Popular choices include Etherscan (for Ethereum-based projects), BSCScan (for Binance Smart Chain projects), and Block Explorer (for Bitcoin).
- Enter the project’s contract address (if applicable) or transaction ID to view the relevant transaction history. Note that not all projects are based on smart contracts.
- Analyze the transaction data. Look for any unusual or suspicious activity. Are there large transfers of funds, repeated transactions to or from specific addresses, or unusually high transaction fees? Such anomalies might signal potential fraud or mismanagement.
- Check the project’s code (if available). Some projects have open-source code. Review the code for any potential vulnerabilities or malicious activity. However, code analysis can be complex and should not be attempted by individuals without the necessary technical expertise.
Using Cryptocurrency News Sources and Forums
Reliable cryptocurrency news sources and forums provide a wealth of information about projects and exchanges. These platforms often publish articles and discussions from knowledgeable individuals, which can help in evaluating a project’s legitimacy and the exchange’s reputation.
- Crucial Considerations: Pay close attention to the source’s reputation and the author’s credentials. Avoid sources that appear biased or are known for spreading misinformation. Look for reputable news outlets and forums with established reputations within the cryptocurrency community.
- Example: A reputable news outlet might publish an article analyzing a new cryptocurrency project, citing its technical details and development team’s background. This helps you form a more informed opinion.
Trusted Sources for Verification
Numerous resources can be used to verify project information and exchange legitimacy.
- Cryptocurrency News Outlets: CoinDesk, CoinMarketCap, Cointelegraph, The Block
- Blockchain Explorers: Etherscan, BSCScan, Block Explorer
- Cryptocurrency Forums: Reddit’s r/CryptoCurrency, BitcoinTalk
Using Regulatory Databases and Government Resources
Regulatory databases and government resources can provide valuable information regarding registered exchanges and projects. This information can help you identify potentially regulated exchanges and ensure they comply with relevant regulations.
- Important Note: Not all cryptocurrencies or exchanges are regulated in every jurisdiction. Regulatory compliance varies significantly across countries and regions.
- Example: The U.S. Securities and Exchange Commission (SEC) maintains a database of registered securities offerings. While not all cryptocurrencies are securities, this information can provide a reference for verifying certain project information.
Handling Suspicious Situations

Source: medium.com
Navigating the crypto world requires vigilance. Fake exchanges and projects often prey on unsuspecting investors. Knowing how to identify and respond to suspicious activity is crucial for protecting your investment and personal information. This section details critical steps to take if you encounter red flags, safeguarding your assets, and reporting fraudulent behavior.Crypto scams are becoming increasingly sophisticated.
Spotting phony crypto exchanges and projects is crucial before diving into the exciting world of long-term investments. Knowing how to identify red flags is key to avoiding scams. Understanding these strategies is essential for smart crypto investments, like those detailed in Essential Strategies for Making Smart Long-Term Cryptocurrency Investment Decisions. But, remember, even with thorough research, always exercise caution and due diligence to protect your hard-earned crypto.
Thorough due diligence is paramount when dealing with any new crypto investment opportunity.
Understanding the tactics employed by fraudsters is essential for avoiding becoming a victim. This section focuses on proactive measures you can take to protect yourself and your finances.
Reporting Suspicious Activity, How to Detect and Avoid Fake Crypto Exchanges and Projects
Recognizing suspicious activity is a critical first step in preventing financial losses. Prompt reporting to the relevant authorities and cryptocurrency exchanges is paramount in combating fraud. Many exchanges have dedicated reporting mechanisms for suspicious transactions and accounts. It is vital to utilize these resources.
- Contacting Relevant Authorities: Report suspicious activity to your local law enforcement agency. They can investigate potential criminal activity and provide assistance in recovering funds. You can also contact the Financial Crimes Enforcement Network (FinCEN) in the US, or equivalent agencies in your jurisdiction. These agencies are often well-equipped to handle crypto-related fraud.
- Reporting to Exchanges: If you suspect fraudulent activity on a specific cryptocurrency exchange, contact their customer support team. Provide details about the suspicious transaction or account. Most reputable exchanges have dedicated channels for reporting suspicious activities. Be prepared to provide relevant transaction details, including timestamps and wallet addresses. Many exchanges have dedicated reporting forms or email addresses specifically for this purpose.
Handling Suspected Victimization
If you suspect you’ve fallen victim to a cryptocurrency scam, swift action is crucial. Taking the right steps can significantly increase your chances of recovering lost funds or preventing further damage.
- Immediate Action: Immediately freeze any accounts associated with the compromised wallet or exchange. Change passwords for all related accounts to prevent further unauthorized access. Document all communication, transactions, and steps you take. This documentation is invaluable for legal proceedings and may be required for any recovery efforts.
- Seek Professional Help: Consult with a cybersecurity expert or a legal professional specializing in financial fraud. They can guide you through the necessary steps to recover lost funds. Be wary of unsolicited advice or offers from unknown sources, and seek assistance from reputable and trustworthy professionals.
- Utilize Recovery Resources: Numerous organizations and platforms provide resources and support for individuals affected by crypto scams. Do your research to identify reliable sources and avoid scams attempting to exploit victims.
Freezing Accounts and Reporting Transactions
A crucial step in responding to suspicious activity is to freeze affected accounts and report suspicious transactions. This is often a necessary measure for protecting your assets and enabling investigation.
- Identify Suspicious Transactions: Carefully review all transactions in your cryptocurrency accounts for any unusual or unauthorized activity. Note the date, time, amount, and recipient or sender of each transaction.
- Freeze Accounts: If you suspect fraudulent activity, immediately freeze any accounts associated with the suspicious transactions. Contact the exchange or platform’s customer support to initiate the account freeze process. Follow the platform’s specific instructions.
- Report Suspicious Transactions: Report the suspicious transactions to the relevant exchange or authorities. Provide detailed information about the transactions, including the date, time, amount, and wallet addresses involved. Document all communication with the exchange or authorities.
Protecting Personal Information
Protecting personal information is paramount when interacting with unverified platforms or projects. Never share sensitive details with unverified entities, as this could lead to identity theft or financial fraud.
- Verify Platforms: Thoroughly investigate any cryptocurrency exchange or project before sharing personal information. Look for reviews, reputable sources, and signs of legitimacy.
- Avoid Sharing Sensitive Data: Never share sensitive personal information, such as full names, addresses, social security numbers, or bank account details, on unverified platforms or with unverified individuals.
- Use Strong Passwords: Utilize strong and unique passwords for all cryptocurrency accounts. Employ two-factor authentication whenever possible.
Summary
In conclusion, safeguarding your crypto investments requires a multifaceted approach. By understanding the red flags, evaluating projects thoroughly, and leveraging external resources, you can significantly reduce the risk of falling victim to fraudulent activities. This guide provides a roadmap to navigate the crypto market with confidence, empowering you to make informed decisions and protect your hard-earned assets. Remember, due diligence is key in the ever-evolving world of crypto.
FAQ Compilation
What are some common red flags to look for in a crypto exchange?
Look for exchanges with poor security measures, a lack of transparency, unrealistic promises, and missing or suspicious licensing information. Be wary of exchanges that lack proper regulatory compliance.
How can I research the legitimacy of a new cryptocurrency project?
Thoroughly investigate the project team’s background, the project’s whitepaper, its roadmap, tokenomics, and community engagement. Look for evidence of genuine community support and avoid projects with suspicious activity or questionable marketing tactics.
What are the best practices for securing my cryptocurrency holdings?
Use strong, unique passwords for wallets and exchanges. Enable two-factor authentication wherever possible. Regularly back up your wallets and avoid sharing sensitive information on unverified platforms. Keep your software updated.
How can I tell if a crypto community is legitimate?
Genuine communities are active, engaged, and transparent. Look for authentic engagement, well-researched content, and a healthy discussion. Be wary of communities with excessive hype, coordinated narratives, or a lack of substance.