How to Secure Your Private Keys to Prevent Crypto Theft
How to Secure Your Private Keys to Prevent Crypto Theft is a crucial aspect of cryptocurrency ownership. Losing or having your private keys compromised can lead to devastating financial losses. This comprehensive guide delves into various security measures, from hardware wallets to password management, to help you safeguard your digital assets.
Understanding the intricacies of private key security is paramount in today’s digital landscape. This post explores practical strategies for securing your crypto investments and keeping your digital wealth safe from theft. From the importance of strong passwords to the risks of phishing attacks, we’ll cover all the critical elements you need to know.
Importance of Private Key Security
Protecting your cryptocurrency holdings hinges on safeguarding your private keys. These seemingly random strings of characters are the gatekeepers to your digital assets, granting access to your funds and control over your cryptocurrencies. Without them, you lose access to your coins. Understanding their critical role and the potential consequences of their compromise is paramount for every cryptocurrency user.Private keys are the bedrock of cryptocurrency security.
They act as unique digital signatures, allowing you to initiate transactions and control your assets. Losing or having your private keys compromised means losing access to your crypto holdings. This loss is irreversible, and there are no recovery options. Imagine the frustration and financial devastation of losing thousands or even millions of dollars in digital assets because of a security lapse.
This emphasizes the critical need for robust security practices.
Crucial Role of Private Keys in Cryptocurrency Security
Private keys are the unique identifiers that grant access to cryptocurrency wallets. They are essential for authorizing transactions and securely controlling your digital assets. They are mathematically linked to your public key, which allows others to send you cryptocurrency. However, only the private key can unlock and authorize the transaction.
Consequences of Losing or Compromising Private Keys
The consequences of losing or having your private keys compromised are severe and irreversible. You lose complete control over your crypto holdings. There’s no way to retrieve your assets once they are lost or stolen. This underlines the importance of meticulous security measures. This irreversible loss can lead to significant financial losses and cause substantial distress.
Difference Between Public and Private Keys
Public and private keys are mathematically linked but distinct. The public key is like your cryptocurrency address, allowing others to send you transactions. It’s essentially a public identifier. The private key is the secret code that controls access to your funds, allowing you to authorize transactions. Imagine your public key as a street address, and your private key as the unique key to your apartment.
Examples of Different Cryptocurrency Private Key Structures
Different cryptocurrencies use varying structures for their private keys. Bitcoin, for instance, employs a 256-bit hexadecimal representation. Ethereum uses a similar structure, also employing a 256-bit representation. The specifics can vary depending on the particular cryptocurrency’s implementation.
Comparison of Crypto Wallet Security Measures
| Wallet Type | Security Measures | Pros | Cons |
|---|---|---|---|
| Desktop Wallets | Often feature strong encryption and offline access options. | Robust security, control over keys. | Potential for malware infection if not properly secured. |
| Mobile Wallets | Typically employ multi-factor authentication and hardware security modules. | Convenient access, often with 2FA. | Vulnerable to phone loss or compromise. |
| Online Wallets | Often rely on strong encryption and security protocols, but security can vary widely. | Convenience, accessibility. | Risk of platform vulnerabilities or hacking. |
| Hardware Wallets | Offline storage and physical security measures. | Highest level of security, physical protection. | Slightly more expensive. |
This table provides a general comparison. The specific security measures of each wallet can vary greatly depending on the provider and the chosen wallet. Choosing a secure wallet and diligently managing your private keys is essential.
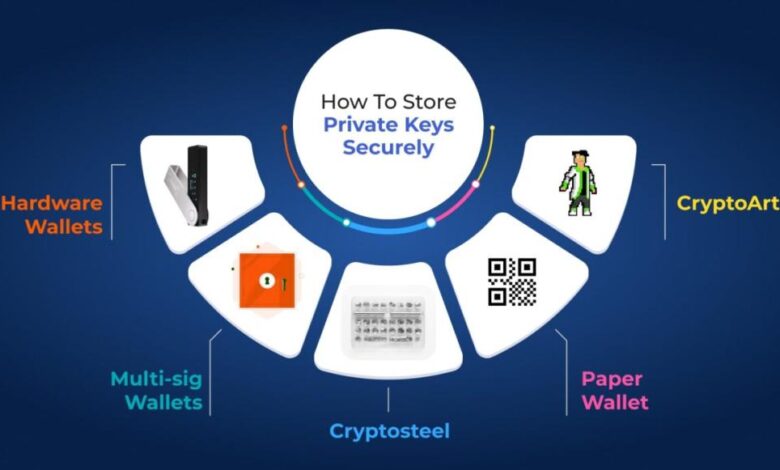
Hardware Wallets
Hardware wallets are a highly secure way to store your cryptocurrency private keys offline, providing a significant layer of protection against online threats. They physically separate your private keys from the internet, making them less vulnerable to hacking, malware, and phishing attacks. This physical separation is crucial for safeguarding your digital assets.Hardware wallets offer a physical device that acts as a secure vault for your private keys.
They are designed to operate independently from your computer or phone, limiting the potential attack vectors. Unlike software wallets, which rely on the security of your device’s operating system and software, hardware wallets provide a dedicated and isolated environment for managing your private keys.
Advantages of Using Hardware Wallets
Hardware wallets provide numerous advantages over other methods of storing cryptocurrency. These advantages include enhanced security, offline access, and tamper resistance. Their physical separation from online environments drastically reduces the risk of compromise.
- Enhanced Security: Hardware wallets are designed with robust security features to protect your private keys. These include advanced encryption, secure chipsets, and tamper-resistant construction. The isolated nature of the hardware wallet’s operation minimizes the impact of a compromised computer or device.
- Offline Access: The primary advantage of hardware wallets is their ability to manage your crypto keys offline. This crucial aspect protects your keys from cyberattacks targeting your connected devices.
- Tamper Resistance: Hardware wallets are built with advanced security measures that make it difficult for malicious actors to gain access to your private keys. These measures can range from physical safeguards to cryptographic protections.
Types of Hardware Wallets
Several hardware wallet manufacturers offer different models with varying features and price points. Each option caters to different needs and security preferences.
- Ledger Nano S/X/S Plus: These wallets are popular choices known for their user-friendly interfaces and robust security features. They are generally considered a solid option for beginners. They employ advanced encryption and security protocols. The Ledger Nano X offers more storage space and enhanced features compared to the Nano S.
- Trezor Model T/One: Trezor wallets are recognized for their strong security measures and sophisticated user experience. They often feature advanced security protocols and dedicated support. The Trezor Model T is a more recent model, offering enhanced features compared to the older Trezor One.
- Coldcard: Coldcard wallets are designed with a focus on extreme security and offline operations. They are often used by advanced users or those with particularly high security needs.
How Hardware Wallets Protect Private Keys
Hardware wallets employ various methods to protect private keys, creating a multi-layered security system. The isolation of the cryptographic hardware within the wallet is a critical aspect of this security architecture.
- Secure Chipset: Hardware wallets utilize secure chipsets that are designed to protect the private keys from unauthorized access. These chipsets operate independently from the device’s main operating system.
- Advanced Encryption: These wallets use sophisticated encryption algorithms to protect the private keys from unauthorized access and manipulation. These algorithms are designed to be resistant to brute-force attacks.
- Offline Operation: Private keys are never transmitted over the internet during operation. All transactions are validated on the hardware device itself, safeguarding against online vulnerabilities.
Comparison of Popular Hardware Wallets
The security features of popular hardware wallets can differ. This comparison emphasizes the varying strengths of each device.
| Hardware Wallet | Security Protocols | Features |
|---|---|---|
| Ledger Nano S/X/S Plus | Secure chipsets, advanced encryption, offline signing | User-friendly interface, multiple coin support |
| Trezor Model T/One | Secure chipsets, offline signing, advanced security protocols | Sophisticated user experience, various recovery options |
| Coldcard | Extreme security measures, offline operation, advanced encryption | Advanced users, maximum security, specialized for offline transactions |
Software Wallets and Security Best Practices

Source: ytimg.com
Software wallets, while convenient, introduce a different set of security considerations compared to hardware wallets. Understanding the various types of software wallets and their inherent vulnerabilities is crucial for safeguarding your cryptocurrency holdings. This section delves into the specifics of software wallet security, from the different types available to best practices for their management.Software wallets come in a variety of forms, each with its own security implications.
Some are browser-based, others are desktop applications, and some are mobile apps. Choosing the right wallet for your needs, and diligently following best practices, is paramount to mitigating risk.
Software Wallet Types and Security Considerations
Software wallets, despite their convenience, can be vulnerable if not managed properly. The security of a software wallet hinges on the strength of its security measures and the user’s adherence to best practices. Understanding the different types of software wallets and their inherent security characteristics is vital.Browser-based wallets often leverage the security of the browser itself, but this protection can be compromised if the browser has vulnerabilities or if the user’s computer is infected with malware.
Desktop wallets are typically more secure as they have greater control over their environment, but they can still be targeted by malware or exploits if the user’s system is compromised. Mobile wallets, while convenient, often rely on the device’s security measures, and vulnerabilities in the operating system or the wallet itself could expose user funds.
Common Security Vulnerabilities in Software Wallets
Several vulnerabilities are frequently associated with software wallets. A critical concern is the potential for malicious software, often disguised as legitimate updates or downloads. This malware can compromise the wallet’s security by stealing private keys or manipulating transactions. Insufficient encryption or flawed code within the wallet itself can be exploited by attackers to gain unauthorized access. Finally, user error, such as poor password management or downloading malicious software, poses a substantial threat.
Best Practices for Secure Software Wallet Management
Proper management of software wallets is essential for protecting your crypto assets. These best practices will help safeguard your investments.
- Strong Passwords and Two-Factor Authentication (2FA): Employing strong, unique passwords for each wallet and enabling 2FA significantly enhances security. Never reuse passwords from other accounts, and consider password managers for secure password storage.
- Regular Updates and Security Audits: Keeping the software wallet updated with the latest security patches is crucial. Regularly reviewing the wallet’s security features and configuration can help identify and address potential vulnerabilities.
- Secure Storage and Handling of Private Keys: Never share your private keys, and never store them in locations that are vulnerable to theft or compromise. Avoid writing down private keys or storing them on unsecured devices.
- Safe Download Sources: Only download software wallets from official and trusted sources. Be cautious of suspicious websites or emails promising free cryptocurrencies.
- Hardware Security Modules (HSMs): Integrating an HSM into your wallet setup can further bolster security, particularly for high-value transactions or when dealing with sensitive data.
Examples of Secure Software Wallet Configurations
Secure configurations vary depending on the specific wallet. However, some general principles apply. Always enable 2FA, use strong passwords, and avoid storing private keys on the same device where the wallet is installed. Consider using a separate computer or device solely for managing crypto assets.
- Offline Wallet Configuration: A secure configuration might involve using a wallet exclusively for crypto transactions, keeping it disconnected from the internet when not in use. This approach minimizes the risk of online attacks.
- Multi-signature Wallet Configuration: For increased security, implement multi-signature functionality in your wallet. This requires multiple parties to authorize transactions, making unauthorized access more difficult.
Comparison of Software Wallet Security Features
| Wallet Type | Security Features | Vulnerabilities |
|---|---|---|
| Browser-based | Leverages browser security; often integrated with exchange platforms. | Browser vulnerabilities, potential for compromised exchange platform. |
| Desktop | More control over environment; generally more secure than browser-based. | Malware infection, compromised operating system, weak encryption. |
| Mobile | Convenient access; often relies on device security measures. | Device compromises, insecure storage of private keys, vulnerabilities in mobile OS. |
Offline Storage and Backup Strategies

Source: calibraint.com
Protecting your crypto private keys is paramount. While hardware wallets offer a high degree of security, having robust offline backup strategies is crucial for safeguarding against unforeseen circumstances like device loss, theft, or malfunction. Offline backups act as a safety net, ensuring you can recover your assets if your primary storage method fails.Offline storage essentially means keeping your private keys away from any connected network or device that could be compromised.
Protecting your crypto requires meticulous private key security. Strong passwords, hardware wallets, and regular audits are crucial. However, if you’re looking to explore passive income streams, understanding how to leverage DeFi platforms like those discussed in How to Leverage DeFi Platforms to Generate Sustainable Passive Income is equally important. Remember, safeguarding your keys is paramount, no matter your crypto strategies.
This separation is vital to prevent malicious actors from accessing your keys directly or indirectly. This approach, coupled with diligent backup practices, significantly strengthens your overall crypto security posture.
Importance of Offline Storage for Private Keys
Offline storage of private keys is critical to prevent unauthorized access. Cybercriminals often target connected devices or networks to steal private keys. By keeping your keys separate from online systems, you minimize the risk of a breach leading to the loss of your crypto holdings. This is akin to keeping your house keys separate from your house; if the house is compromised, you still have the key to access your valuables.
Secure Methods for Creating and Storing Offline Backups
Creating and storing offline backups requires careful consideration. A crucial aspect is the physical security of the storage medium. Use robust, tamper-resistant containers for storing backup files.
Best Practices for Managing Offline Backup Files
Managing offline backup files involves several best practices to maintain their security and integrity. First, create multiple copies of your backups and store them in different locations. This approach minimizes the risk of losing all your backups in a single event. Consider a physical vault or a secure, offsite storage solution. Secondly, use strong passwords or passphrases for protecting your backup files.
Furthermore, ensure that your backup files are stored in an encrypted format. This way, even if the physical media is compromised, the content remains inaccessible without the decryption key.
Importance of Paper Wallets and Their Security Implications
Paper wallets provide a simple yet effective offline storage method for private keys. They consist of printed QR codes or key information that represent your private keys. However, they have inherent security implications that must be addressed. The physical nature of paper wallets makes them susceptible to loss, damage, or theft. Proper handling and storage are essential.
Creating Secure Paper Wallets
Creating secure paper wallets involves generating and storing keys safely. Use a reputable, trusted cryptocurrency wallet generator or a reliable online tool. Ensure the keys are generated and saved in a secure offline environment. Verify the information printed on the paper wallet meticulously to prevent errors. Storing the backup file in a waterproof and fireproof environment is also vital.
Print the private key information on high-quality, archival-grade paper. Store the paper wallet in a secure location, separate from the computer or device used to generate it. Furthermore, it’s essential to never share or disclose the paper wallet’s private keys with anyone.
Password Management and Security
Protecting your cryptocurrency investments hinges on the security of your private keys, and a critical component of this is robust password management. Weak passwords can be easily compromised, leading to the theft of your entire crypto portfolio. Strong password practices are paramount to preventing unauthorized access to your wallets and maintaining control over your digital assets.
Importance of Strong Passwords
Strong passwords are essential for safeguarding cryptocurrency wallets. They act as the first line of defense against unauthorized access. A weak password, on the other hand, can be easily cracked using readily available tools and techniques. Compromised passwords can lead to the theft of funds, and the recovery process can be complex and time-consuming. A strong password is characterized by its complexity and length, making it difficult for attackers to guess or crack.
Password Management Best Practices
Implementing effective password management practices is crucial for protecting your cryptocurrency wallets. These practices go beyond simply creating strong passwords. They encompass the entire process of managing and storing your passwords securely. Creating unique and complex passwords for each account is paramount. Avoid using easily guessed passwords like birthdays, names, or common phrases.
Utilizing a password manager is strongly recommended for generating and storing strong, unique passwords across multiple accounts.
Different Password Management Tools and Their Security Strengths
Various password management tools are available, each with its own security strengths and weaknesses. Some popular options include LastPass, Bitwarden, and 1Password. These tools offer features such as password generation, storage, and auto-filling, making password management easier and more secure. Choosing a reputable password manager with robust encryption and multi-factor authentication is crucial. Always prioritize tools with a strong track record of security and user reviews.
Multi-Factor Authentication (MFA)
Multi-factor authentication (MFA) adds an extra layer of security to your cryptocurrency wallets. Beyond a password, MFA requires a second form of verification, such as a code from an authenticator app or a security key. This two-step verification process significantly reduces the risk of unauthorized access, even if a password is compromised. Implementing MFA strengthens the overall security posture of your cryptocurrency accounts.
Password Security Guidelines and Best Practices
| Category | Guidelines and Best Practices |
|---|---|
| Password Complexity | Use a combination of uppercase and lowercase letters, numbers, and symbols. The longer the password, the more secure it is. Avoid using easily guessable information. |
| Password Uniqueness | Create unique passwords for each account. Do not reuse passwords across different platforms. |
| Password Storage | Utilize a reputable password manager to securely store your passwords. Never write down your passwords. |
| Multi-Factor Authentication | Enable MFA whenever possible to add an extra layer of security to your accounts. |
| Regular Password Updates | Change your passwords regularly, especially if you suspect a security breach. |
| Avoid Weak Passwords | Never use easily guessable passwords like birthdays, names, or common phrases. |
Recognizing and Avoiding Phishing Attacks
Phishing attacks are a significant threat to cryptocurrency users, aiming to trick individuals into revealing sensitive information like private keys. These attacks often leverage social engineering tactics, exploiting human psychology to manipulate victims into taking actions that compromise their security. Understanding these tactics and recognizing the red flags associated with phishing attempts is crucial for protecting your cryptocurrency assets.
Phishing Attack Methodology
Phishing attacks employ various methods to target cryptocurrency users. They often mimic legitimate platforms or services, creating convincing imitations of websites or emails. These fraudulent communications aim to gain access to your private keys, either directly or by tricking you into revealing them. Attackers use social engineering to manipulate users into clicking malicious links or downloading harmful attachments.
Phishing attacks can be launched through various channels, including email, text messages, and even social media.
Common Phishing Tactics
Phishing attacks frequently use deceptive tactics to trick users. These include creating fake websites that closely resemble legitimate cryptocurrency exchanges or wallets. Attackers might also send emails that appear to be from reputable companies or individuals, prompting users to click links or open attachments containing malware. Spear phishing, a more targeted approach, involves sending emails that appear to be personalized and relevant to the recipient, making them more likely to fall for the scam.
Verifying Website and Email Authenticity
Verifying the authenticity of websites and emails is essential to avoid falling victim to phishing attacks. Always check the website’s URL for any inconsistencies or suspicious characters. Look for the presence of secure connections (HTTPS) and legitimate security certificates. Be cautious of emails with poor grammar, typos, or generic greetings. Contact the organization directly if you have doubts about the authenticity of a communication.
Red Flags to Watch Out For
Several red flags can indicate a potential phishing attempt. Urgent requests for immediate action, unusual or unexpected requests for personal information, and generic greetings are strong indicators of a scam. Phishing attempts often include threats or promises of rewards to pressure you into acting quickly. Suspicious links, unfamiliar email addresses, and poor formatting are also significant red flags.
Common Phishing Email Subject Lines to Avoid
- Urgent: Your Account Has Been Compromised
- Important Security Notice Regarding Your Cryptocurrency Account
- Claim Your Cryptocurrency Reward Now!
- Verify Your Cryptocurrency Wallet Details
- You Have Won a Cryptocurrency Prize!
- Important Update Regarding Your Recent Transaction
- Verification Required for Your Recent Purchase
- Your Cryptocurrency Wallet Has Been Locked
These are just a few examples, and the subject lines used in phishing attempts are constantly evolving. Critically evaluate any email or message that appears urgent or suspicious, regardless of the sender’s apparent legitimacy.
Security Audits and Regular Assessments
Regular security audits are crucial for maintaining the safety of your cryptocurrency holdings. Just like a yearly check-up for your physical health, a security audit for your crypto wallet helps identify vulnerabilities and potential risks before they lead to costly losses. Proactive assessments prevent unforeseen breaches and ensure your assets remain protected.
Importance of Regular Audits
Regular security audits are vital for maintaining the integrity and security of your cryptocurrency wallet. These audits provide a comprehensive evaluation of your security posture, uncovering weaknesses and potential threats. This proactive approach allows for timely mitigation of risks, reducing the likelihood of compromise. Thorough audits are essential for ensuring the safety and reliability of your crypto holdings, helping you avoid financial losses.
Process of Conducting a Security Audit
A security audit involves a systematic evaluation of your wallet’s security practices. This includes scrutinizing your wallet’s software, storage methods, and access controls. The audit should cover all aspects of your crypto ecosystem, from the hardware wallet to your online interactions. It’s important to be thorough and methodical in your assessment. A checklist can help guide the process and ensure no aspect is overlooked.
Types of Security Assessments
Various assessments can be performed to evaluate your wallet’s security. A critical aspect is the assessment of the software itself. This involves checking for known vulnerabilities, examining update logs, and confirming the software version. Another key component is evaluating your hardware wallet’s security. This includes assessing the physical security of the device and the strength of its security protocols.
Reviewing your backup strategies is also essential. This includes evaluating the security of your backup location and the strength of the encryption used. Lastly, assess your online interactions, ensuring robust password management, multi-factor authentication (MFA), and secure communication protocols are in place.
Detecting and Mitigating Potential Threats
Detecting potential threats requires a careful examination of your wallet’s security posture. Suspicious transactions, unusual login attempts, and phishing attempts should be flagged and investigated. Reviewing transaction history for any discrepancies is essential. Identifying potential malware or viruses on your device is also critical. Implementing strong security measures, such as multi-factor authentication, can significantly mitigate the risk of unauthorized access.
Regular software updates and patches can help to address any known vulnerabilities.
Protecting your crypto requires strong private key security, a crucial aspect of responsible trading. Understanding how to safeguard these keys is paramount, especially when considering the broader strategies for successful cryptocurrency trading, such as those outlined in Essential Risk Management Techniques for Successful Cryptocurrency Trading Today. Ultimately, robust security practices, including careful key management, are essential for avoiding theft and maximizing your cryptocurrency gains.
Simple Checklist for Assessing Your Wallet’s Security Posture
- Software Updates: Verify all software (desktop, mobile) is updated to the latest versions. Outdated software often has known vulnerabilities. Check the update logs to ensure that recent updates have been applied successfully. If the software has any security patches, implement them immediately.
- Hardware Security: Evaluate the physical security of your hardware wallet. Ensure it is stored in a secure location, away from potential theft or damage. Consider a secure, locked location. If the wallet is a physical device, ensure it is not easily accessible to others.
- Backup Strategies: Review your backup strategies to ensure they are secure and readily accessible. Evaluate the security of your backup location. Implement strong encryption to protect your backup data.
- Password Management: Review your password management practices. Ensure strong passwords are used for all accounts associated with your cryptocurrency wallet. Utilize a password manager for complex and unique passwords. Avoid reusing passwords for different accounts.
- Online Interactions: Scrutinize your online interactions. Identify and avoid phishing attempts. Use trusted sources for information related to your wallet and cryptocurrencies. Use HTTPS for all online transactions and communications. Verify the legitimacy of websites and services you interact with.
Protecting Against Malware and Viruses
Cryptocurrency, with its decentralized nature, presents a unique set of security challenges. One significant threat comes from malicious software, or malware, designed to exploit vulnerabilities in cryptocurrency wallets and steal funds. Understanding the types of malware and implementing robust security measures is crucial for safeguarding your digital assets.Malware targeting cryptocurrency wallets can range from simple phishing scams to sophisticated ransomware attacks.
These threats can infiltrate systems in various ways, from infected email attachments to compromised websites. Protecting your wallets requires proactive measures and vigilance.
Risks of Malware and Viruses Targeting Cryptocurrency Wallets
Malware targeting cryptocurrency wallets can lead to significant financial losses. Criminals can use various methods to gain access to your private keys, potentially leading to the theft of your entire cryptocurrency holdings. Furthermore, some malware can lock your wallet or demand ransom before returning access. This can result in significant financial losses and a disruption to your financial activities.
Different Types of Malware Targeting Cryptocurrency Wallets
Various types of malware target cryptocurrency wallets, each with its unique method of operation. Phishing attacks are common, tricking users into revealing their private keys through deceptive emails or websites. Ransomware, another prevalent threat, encrypts your wallet data and demands payment to restore access. Cryptojacking is a form of malware that secretly uses your computer’s resources to mine cryptocurrency, reducing your device’s performance and potentially draining your battery life.
Protecting your private keys is crucial for preventing crypto theft, but equally important is diversifying your holdings. A strong strategy involves not just securing your keys, but also spreading your investments across different cryptocurrencies, like the approach detailed in this excellent guide on How to Build a Diversified Crypto Portfolio for Maximum Gains. Ultimately, both robust key management and smart portfolio building are essential steps in navigating the crypto world safely and profitably.
Spyware can monitor your online activities, including wallet transactions, and gather sensitive information to steal your cryptocurrency.
Identifying and Removing Malicious Software
Identifying and removing malicious software is essential for safeguarding your cryptocurrency assets. Pay close attention to unusual system behavior, such as slow performance, pop-up windows, or unexpected changes in your wallet software. Regular scans with reputable antivirus software can help detect and remove malicious programs. If you suspect an infection, immediately isolate the affected device to prevent further damage.
Consult a cybersecurity professional for assistance in complex cases.
Importance of Regularly Updating Your Software and Operating Systems, How to Secure Your Private Keys to Prevent Crypto Theft
Regularly updating your software and operating systems is crucial for mitigating security vulnerabilities. Software updates often include critical security patches that address known vulnerabilities, protecting your system from malware. Failing to update leaves your system susceptible to exploitation by hackers and malware authors. Staying updated with the latest software versions is essential to protect your cryptocurrency holdings.
Recommended Antivirus Software for Protecting Crypto Wallets
| Software Name | Description | Pros | Cons |
|---|---|---|---|
| Bitdefender | A comprehensive antivirus solution with strong detection capabilities. | High detection rate, robust protection against various threats. | Can be resource-intensive on older systems. |
| Norton AntiVirus | A well-known and trusted antivirus with a user-friendly interface. | Wide range of features, user-friendly interface, available on multiple platforms. | Performance might be slightly slower compared to other solutions. |
| Kaspersky Anti-Virus | Known for its strong protection against malware and viruses. | Good protection against malware, wide range of features. | May have a higher resource usage on some systems. |
| Malwarebytes | Specialized in detecting and removing malware, including rootkits and ransomware. | Effective at removing persistent threats, strong real-time protection. | Might be less comprehensive than a full antivirus solution. |
This table provides a starting point for choosing antivirus software. Thorough research and consideration of your specific needs and system requirements are essential.
Security Measures for Mobile Wallets: How To Secure Your Private Keys To Prevent Crypto Theft
Mobile wallets, while convenient, present unique security challenges. Their reliance on smartphones, often exposed to physical risks and digital threats, necessitates careful consideration of security measures. Understanding these risks and adopting best practices can significantly reduce the likelihood of crypto theft.Mobile wallets offer streamlined access to cryptocurrencies, but they require a heightened awareness of security protocols to protect against potential compromises.
Users must diligently implement security measures and regularly update their practices to keep pace with evolving threats.
Mobile Wallet Security Considerations
Mobile wallets, while offering convenience, inherently introduce security risks. These risks stem from the vulnerability of smartphones to physical theft, malware, and social engineering attacks. Mobile wallets store sensitive private keys, making their security paramount.
Best Practices for Using Mobile Wallets Securely
Implementing robust security practices is crucial for safeguarding cryptocurrency held within mobile wallets. These practices should encompass both physical and digital security measures.
- Strong Passwords and Multi-Factor Authentication (MFA): Employing strong, unique passwords for mobile wallets, combined with robust MFA, adds an extra layer of security. Using a password manager can aid in generating and remembering complex passwords.
- Regular Updates and Security Patches: Keeping the mobile wallet application and operating system updated with the latest security patches is vital. These updates often include critical fixes for vulnerabilities.
- Two-Factor Authentication (2FA): Implementing 2FA adds another layer of security. This involves receiving a one-time code via SMS or authenticator app upon login, significantly increasing security.
- Avoid Public Wi-Fi: Avoid using public Wi-Fi networks to access or interact with your mobile wallet. These networks are often less secure and can be exploited by malicious actors.
Potential Security Risks Associated with Mobile Wallets
Several potential security risks are inherent to mobile wallets. Understanding these risks is crucial for implementing appropriate security measures.
- Physical Theft: A lost or stolen phone containing a mobile wallet can expose private keys to unauthorized access.
- Malware and Viruses: Malicious software can compromise the phone and steal private keys.
- Phishing Attacks: Phishing attempts can trick users into revealing their login credentials or installing malicious software.
- Social Engineering: Sophisticated social engineering tactics can manipulate users into revealing sensitive information, including wallet credentials.
Configuring Mobile Wallets for Enhanced Security
Proper configuration is essential for bolstering mobile wallet security. Users must carefully review and adjust settings to minimize vulnerabilities.
- Enable Device Lock: Enable a strong screen lock (e.g., PIN, password, fingerprint) on the mobile device to prevent unauthorized access if the phone is lost or stolen.
- Use a Secure VPN: A VPN can encrypt your internet connection, protecting your data when accessing your mobile wallet over public Wi-Fi networks.
- Review and Adjust Privacy Settings: Thoroughly review and adjust privacy settings within the mobile wallet application to restrict access to sensitive data.
Comparison of Security Measures of Different Mobile Wallets
Various mobile wallets offer different levels of security. A comparative analysis can help users choose a wallet with suitable security measures.
| Wallet | Security Features | Strengths | Weaknesses |
|---|---|---|---|
| Wallet A | Biometric authentication, two-factor authentication, regular security updates | Strong security measures | Potentially higher cost or complexity |
| Wallet B | Basic authentication, limited security features | Simple to use | Vulnerable to attacks |
Different wallets implement various security protocols. A critical evaluation of available options and selection based on individual needs is vital.
Ending Remarks
In conclusion, securing your private keys is an ongoing process that requires vigilance and proactive measures. By implementing the strategies Artikeld in this guide, you can significantly reduce the risk of crypto theft and protect your hard-earned digital assets. Remember, a proactive approach to security is key to preserving your financial well-being in the ever-evolving world of cryptocurrency.
FAQs
What are the most common types of crypto wallets?
Common wallet types include hardware wallets, software wallets, mobile wallets, and paper wallets. Each has its own security strengths and weaknesses.
How often should I update my software and operating systems?
Regular updates are crucial to patch security vulnerabilities and protect against malware. Stay current with security patches.
What are some red flags to watch out for in phishing emails?
Suspicious email addresses, urgent requests for information, and poor grammar or spelling are common red flags. Verify the authenticity of emails and websites before clicking on links or sharing information.
What is multi-factor authentication (MFA) and why is it important?
MFA adds an extra layer of security by requiring more than one form of verification (e.g., password and code). This makes it harder for attackers to access your accounts even if they have your password.